Unfortunately, there’s no way to completely protect your business against cyber attacks. This is particularly the case with malware infections. Malware is ‘malicious software’ delivered into your network via code or files in links and attachments that infect, steal or manipulate your data.
Therefore, it’s highly important to have high levels of defence in place.
The most common routes of cyber attacks over the last couple of years have been:
- The internet of things – IOT devices capturing and transporting data are particularly vulnerable to cyber criminals looking for weaknesses and opportunities for data thefts.
- Mobile phones and tablets connected to organisations networks and data
- Third party software or supply chain security risks
- Working from home.
This means cyber security should be at the top of every company’s IT security agenda.
How can you integrate cyber security processes into your business to safeguard against cybercrime and data breaches?
Here are five points to consider.
1) Implement Multi-Factor Authentication and password management
Even though Multi-Factor Authentication (MFA) is straightforward to implement, we are surprised at the number of IT audits we carry out where MFA hasn’t been set up.
MFA provides an extra layer of security, usually a second piece of information that you provide when logging into an online system and is standard in Office 365.
In a recent article, the Chartered Institute of IT reviewed IBM’s Cost of Data Breaches Report 2022, which stated that ‘misconfigured Cloud’ is responsible for 15% of cyberattacks.
Regarding passwords, it’s impossible to remember a unique password for every account and application you have, so we highly recommend randomly generated passwords held in a password manager.
The password manager you choose must:
- Store everything in an encrypted state (account names, companies and URLs, as well as the passwords)
- Keep a record of your last few passwords for any given application just in case
- Be easy to backup and restore
- and it’s useful if the password manager can sync between multiple devices
2) Patch Management to address vulnerabilities
Vulnerabilities in third-party software accounts for 13% of cyber attacks. A high percentage of these originate from software that’s not been updated; a fact that cyber criminals depend on.
To reduce the risk of a cyber attack every business should have a Patch Management process. Software updates can be automatically monitored for new releases. Urgent updates can be made immediately. In our experience there are some instances where it can be prudent to wait before implementing the patch.
Software updates not only protect your IT infrastructure from cyber attacks they can also include new features or functionality, enhancing the benefit of the software for the user.
If you have a bespoke software solution this can increase the level of risk, because you are reliant on the developer to keep the software up to date and cyber secure.
3) Cyber security training
In the same article, the Chartered Institute of IT noted that credential theft accounted for 19% of cyber attacks and phishing accounted for 16%.
Both of which can be considerably reduced through an employee training programme so that phishing, scam and malicious email (or even telephone calls) can be spotted.
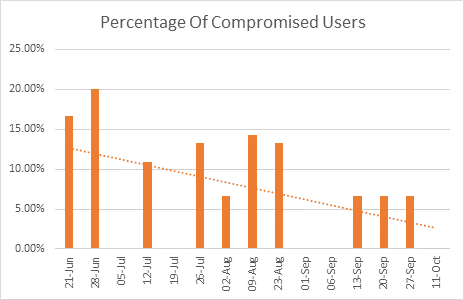
A recent cyber security training that we carried out reduced the instances of staff clicking on suspicious links by 60%.
4) Backups
Your backup procedure is your safety net should, for whatever reason, 1) MFA and password management, 2) patch management or 3) cyber security training fail or be neglected. And even if you have strong processes and procedures in place for 1, 2 and 3 the same degree of importance should be associated to your backup procedures. Here’s more information about backup:
Part 1 – It’s perfectly safe, it’s all in the Cloud
Part 2 – What you need to know about Local and Cloud Back-up
Part 3 – 6 Security weak points to check when you move to the Cloud
Part 4 – When it’s business critical how reliable is the Cloud?
5) Plan and test your recovery process
Should you be the victim of a data breach having a disaster recovery plan will allow you to quickly set in motion the actions needed to reduce the effects on your business, employees, customers, suppliers and other stakeholders.
A plan ensures that everyone knows their roles and responsibilities, which means you can act quickly and contain or reduce the damage.
Your plan should be tested with every scenario in mind whether this be an incidence of fire, flooding or ransomware.
So, how can you safeguard your business against cyber attacks?
High on the 2023 list of cyber security predictions is an increase of ransomware and a rise in cloud breaches due to the amount of valuable data stored in the cloud.
We recommend that you carry out an IT audit to identify gaps and areas of vulnerability within your business. This will allow you to take the necessary actions to mitigate the risks.
We’ve created a quick and simple questionnaire to help you carry out an IT audit. The areas covered include IT policies, processes, network, equipment and software. You’ll receive a report with your results immediately on completion.